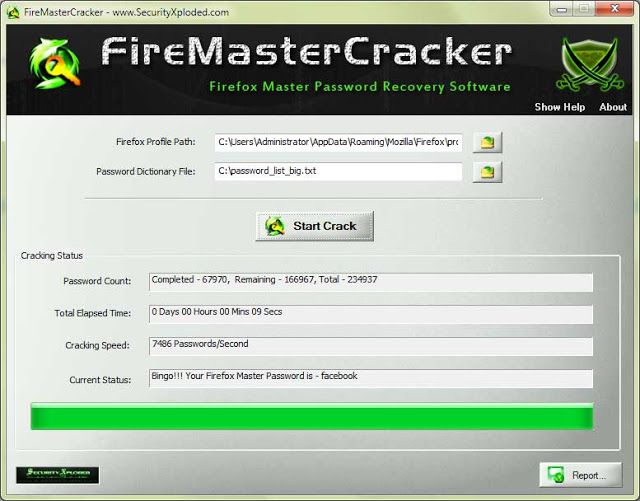
Cracking Software
Jun 02, 2019 • 46 views
CRACKING
A crack could be a methodology for breaking into a secured ADPS.
It was coined in the 1980s by hackers who wanted to disassociate themselves from the more malicious practices carried out by hackers.
A cracker’s sole purpose is to interrupt into a system, gaining fulfillment from being able to “crack” the system's security shield.
Real hackers transcend simply gap up a system.
They go within the system to achieve information and data for malicious intent, devilish pranks, and profiteering.
The term crack is additionally usually applied to the files utilized in code-cracking programs, that change hot repeating and therefore the use of economic code by breaking (or cracking) numerous
registration and copy-protection techniques.
How Do People Crack Computer Programs And Games?
First step: Think like a user.
This entails understanding the program itself, in its unrestricted kind.
For example, this might be a chunk of software package with a 30-day full-featured trial, and once the test period is over the software package application, not function.
Before somebody develops a crack, they usually got to perceive what undesirable options area unit gift or what options area unit left to be desired.
Adding options is sometimes referred to as “modding”, that is considerably more durable than “cracking” (disabling bound features).
Hypothetically, if a cracker is making an attempt to avoid a license for a game, she might need to shop for the sport for herself and beat the sport from beginning to end
to try and perceive what a “full-featured” system feels like.
Second step: Think like an architect.
Specifically, the cracker puts herself within the mentality of the appliance engineer so as to do and guess however the undesirable feature was enforced.
For example, a naive implementation of a 30-day trial package may add a key-value to the Windows written record (if running on Windows OS), and at startup, check if the
the current timestamp is older than the written record price by but thirty days.
This forms the idea of however the cracker can approach the matter.
Some straightforward tests the cracker may perform is to visualize if straightforward hacks like wiping the written record price or setting the clock back in time will bypass these options.
Third step: Think like a mechanic.
Reverse-engineering a chunk of the software package is incredibly very like taking an automobile apart and golf stroke it back at the side of a blindfold on - you’re not even specifically certain what automobile
the model you’re disassembling, however, you roughly savvy an automobile works and might feel together with your hands what items connect with one another, what components are essential for the automobile
to function, etc.
Technically, all you wish to crack a chunk of software package could be a text editor which will edit positional representation system values in an exceedingly binary (Hex editor software package is well-suited to this).
Cracking a chunk of software package ultimately boils right down to overwriting a number of alternative bytes in an exceedingly binary.
