New Malware Infected 25 Million Devices In India From Pre-Installed App
Jul 15, 2019 • 6 views
if you clicked on popular apps like WhatsApp, temple run etc but still get advertisements then your device might be infected with this malware.
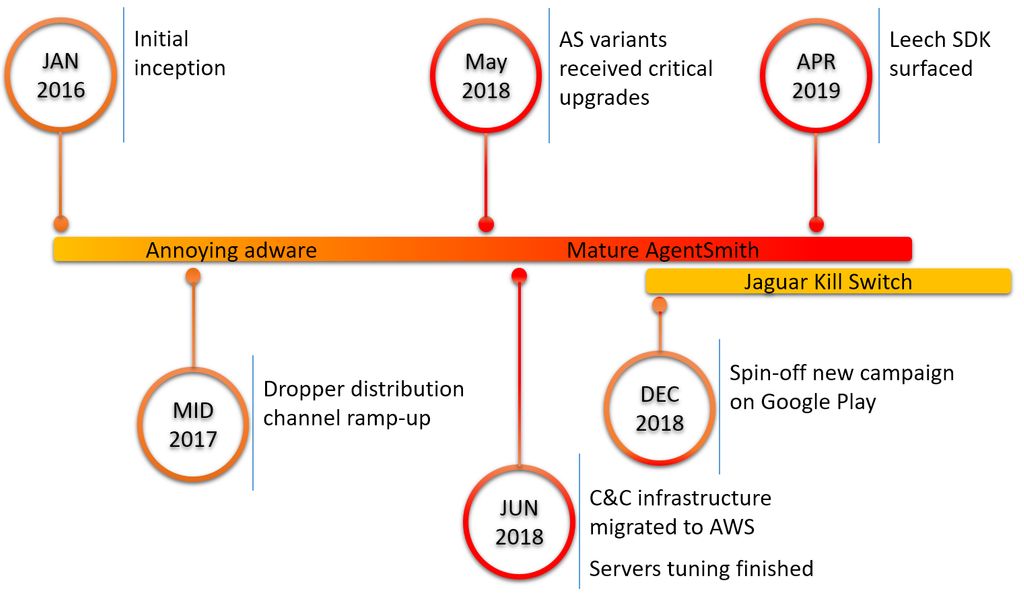
A new type of malware is being discovered by the security firm "checkpoint" has infected more than 25 million devices with Indian users having largest share. it is distributing from a pre-installed app in some android devices. the malware is codenamed "Agent Smith".
yeah,sounds familiar that's the name of main antagonist of the matrix film. the malware gets its name due to methods it uses to attack on android , without even letting anyone noticed about it.
why it is dangerous?
the agent Smith disguised itself as a Google related app and exploits the known vulnerabilities of android versions.
it automatically replace the apps installed in the devices with the malicious versions of the apps we k even without user's interaction or knowledge.
currently, it only shows fraudulent ads for financial purpose only but can also be used for other dangerous purposes like stealing of bank credentials, eavesdropping, sending users private photos (also videos) etc.
it do these task in background and also conceals its icon so, it is very challenging to remove it by the common users on their own.
the researchers at checkpoint day that they discovered the malware in early 2019. it is the stealth infection methodology that complicates the thing, which makes it hard to detect until the device has been compromised.
origin of Agent Smith
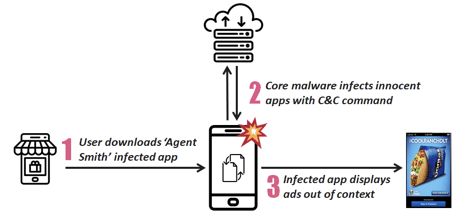
the checkpoint says that it was mainly downloaded from the 9apps store. the 9apps store is a third-party application store that is managed by UC-web. the name sounds familiar, yeah it is as the developers are also responsible for running the UC browser.
the 9app is pre-installed in various smartphones such as Micromax, Intex etc. the current speculation is that the current version of Agent Smith appeared in early 2018.
the apps hard-coded in malware
the list of apps that are hard-coded in the malware's code are:
• com.whatsapp
• com.lenovo.anyshare.gps
• com.mxtech.videoplayer.ad
• com.jio.jioplay.tv
• com.jio.media.jiobeats
• com.jiochat.jiochatapp
• com.jio.join
• com.good.gamecollection
• com.opera.mini.native
• in.startv.hotstar
• com.meitu.beautyplusme
• com.domobile.applock
• com.touchtype.swiftkey
• com.flipkart.android
• cn.xender
• com.eterno
• com.truecaller
how to prevent it?
uninstall the 9app, if it is installed on your smartphone and also the apps downloaded through it.
most of the android devices are of android 5(lollipop) and 6(marshmallow), as android 7(nougat) fixed the vulnerability by introducing APK signature Shceme V2. So, if your device recieve update, so update it.
if you have installed any of the above apps, then also uninstall it and do a hard reset of the device
update:
checkpoint also noticed in recent months, they found several apps with components of Agent Smith have started appearing in the play Store.
it detected 11 such apps. but today morning, it removed 14 such apps.